NullRabbit Progress Update - Nov 20 2025
Architecture Updates
Regrettably, early flows are oftentimes lost in time and space. But they serve as a memory of how things started, evolved, and sometimes disappeared entirely. This diagram represents one of those foundational artifacts - a snapshot of NullRabbit Guard's packet processing architecture as it exists today.
Deployment Architecture
NullRabbit Guard is written in Rust and C, designed to run at the kernel level for maximum performance. While it can be installed directly on a validator node, the recommended deployment model separates concerns for better security and network segmentation:
- Network Gateway/Bastion: Deploy as a dedicated network endpoint or bastion host in front of your validator infrastructure
- Cloud Agnostic: Works seamlessly on Google Cloud (GCE), AWS, and bare metal environments
- Defense in Depth: By running Guard on a separate instance, you isolate threat detection from your critical validator nodes
This separation ensures that even under attack, your validator's resources remain dedicated to consensus operations while Guard handles the incoming traffic storm.
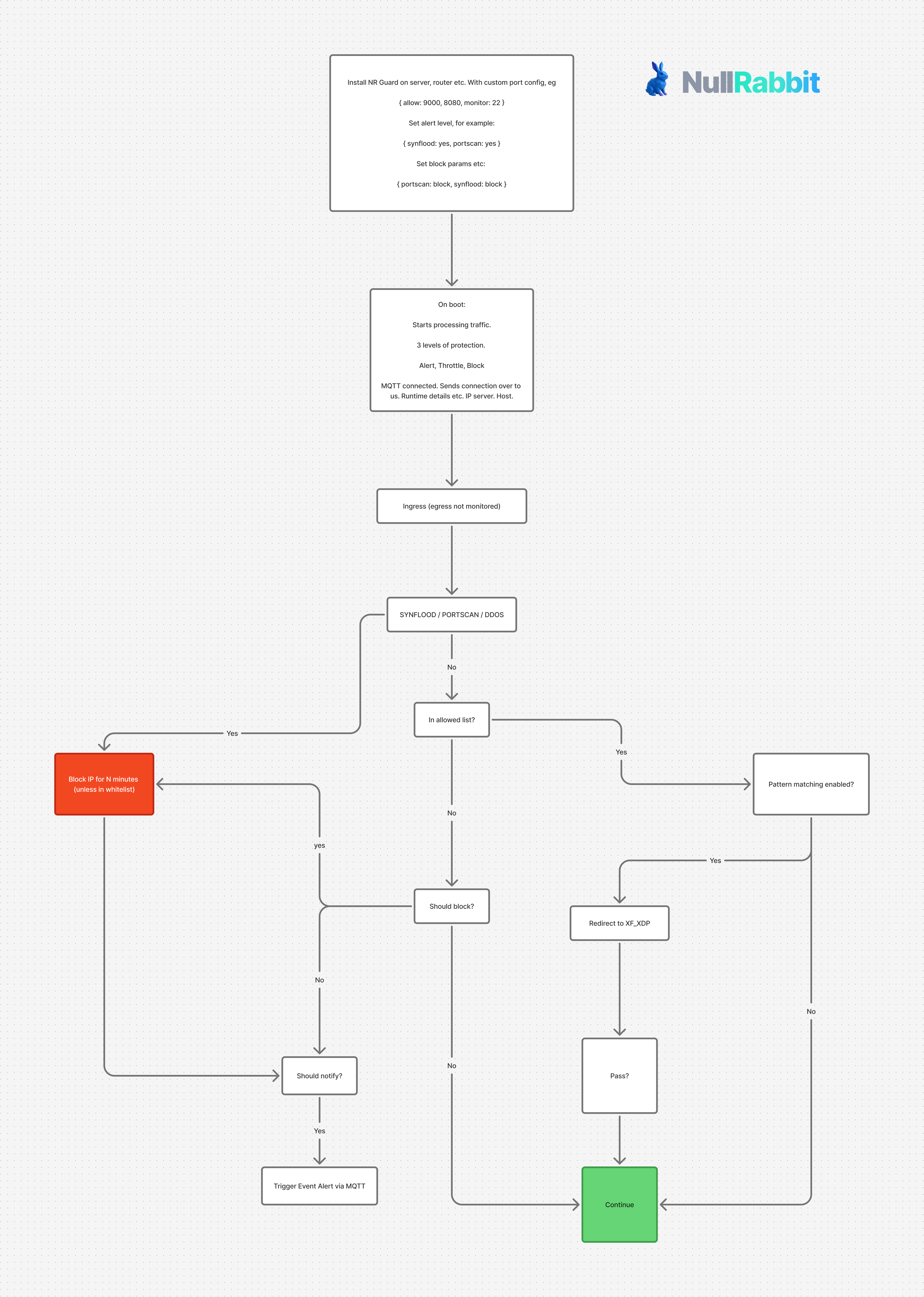
How It Works
The flow diagram above shows Guard's packet processing pipeline. Traffic enters at the kernel level, where our XDP/eBPF hooks intercept packets before they traverse the network stack. This early interception is critical - by the time a packet reaches userspace, you've already paid the performance cost.
Guard currently detects and mitigates three major threat categories:
- DDoS and Flood Attacks: SYN floods, packet floods, and volumetric attacks are dropped at the driver level before socket allocation
- Protocol Exploits: Malformed packets and protocol-level vulnerabilities are caught through deep packet inspection
- Anomaly Detection: Suspicious traffic patterns trigger alerts and can be automatically blocked based on configurable thresholds
Performance Characteristics
In development testing on a Debian VM with 8GB RAM, Guard is showing exceptional efficiency:
- CPU Overhead: Maintained at less than 2% - kernel-level processing avoids userspace context switches
- Memory Footprint: Minimal RAM usage thanks to zero-copy packet handling
- Latency Impact: Near-zero added latency for legitimate traffic
We're currently building a comprehensive benchmarking suite to quantify these characteristics under realistic attack scenarios. Expect formal performance numbers in an upcoming post.
What's New
The past few weeks have seen significant improvements across the board:
Architecture Refinements: We've streamlined the packet processing flow to reduce decision points and improve cache locality. The result is faster packet filtering with lower jitter.
New Detection Capabilities: Guard now includes pattern-based anomaly detection that learns normal traffic baselines and flags deviations. This catches zero-day attack patterns that signature-based systems miss.
Performance Optimizations: By moving more logic into eBPF and optimizing our Rust control plane, we've reduced CPU overhead by approximately 30% compared to the initial implementation.
MQTT Integration: Guard now publishes telemetry and alerts via MQTT, enabling real-time monitoring. However, this is currently one-way communication - we haven't yet implemented the bi-directional feedback system where Guard dynamically adjusts filtering rules based on downstream validator health signals.
What's Next
Production Deployment: The primary focus now is hardening Guard for production use. This includes:
- Comprehensive load testing under simulated attack conditions
- Formal performance benchmarking with published metrics
- Security audit of the eBPF programs and Rust codebase
- Integration testing with major validator clients across different chains
Closing the Loop: We're working on the bi-directional communication layer that will allow Guard to receive feedback from validators and adjust filtering policies in real-time. This creates a closed-loop defense system where threat response is informed by actual validator performance metrics.
Technical Deep Dive
For those interested in the implementation details, Guard's architecture leverages:
- XDP (eXpress Data Path) for kernel-level packet filtering
- eBPF programs written in Rust using the Aya framework, compiled with bpf-linker (which uses LLVM) to eBPF bytecode
- Rust for the userspace control plane and configuration management
- Zero-copy networking to minimize memory overhead
- Lock-free data structures for high-concurrency packet processing
We'll be publishing technical deep dives on specific components in future posts, including our eBPF program structure and the Rust control plane design.
Further anomalies will be logged and dispatched in the next window. Stand by for further directives.
